
Information Security Management – View through the Digitization lens
Until about 5 years back, most of the organizations would consider the scope of their Information Security management as largely consisting of the policies, procedures, and guidelines to manage their IT systems, networks, applications, databases, and data. The controls always revolved around people, process, and technology aspects. From the initial days of having fixed perimeter and total ownership, to where we are today, that perimeter has completely dissolved. Because today’s business is dependent upon the cloud for growth and IOT for innovation.
Hence, it is essential for organizations to adapt to today’s complex security landscape where there is no longer a single perimeter.
- Whether you are providing customer and third-party access to certain systems and data
- Allowing employees to use their own smartphones and laptops, or using apps Software-as-a-Service (SaaS) vendors
- Or taking advantage of multiple cloud providers
Many organizations have a fragmented approach towards addressing their security management framework today. The reasons may range from rapid digitization, the non-coordinated journey to the cloud, and loosely integrated IT/OT/IoT infrastructure. Lack of a comprehensive and orchestrated approach to managing security will result in missing some of the critical threat vectors, vulnerabilities, and pertinent risks.
With the increase in technology shift, organizations tend to ignore the need to update their ISMS documentation to reflect “Practice what is documented and document what is to be practiced”. How much ever sophisticated the systems that one has in place, this will bring down the maturity level from “Level 5: optimized” to “Adhoc”. This calls for an urgent review of current Information security management practices in the organization and revamps of the associated processes to address them. The process shall also address how do we optimally use the resources and practices to bring a more coordinated approach between various business and technology functions within and supporting the organizations.
Here are some of the questions that the internal security management functions must ask to assess their current state of IT Security Management;
- Is your current Information security management system covers all organization boundaries?
- Is there alignment across your organization’s digitization strategy?
- Are you able to realign policies, practices, and procedures based on the organization’s current digital backbone, compliance, and regulatory requirements?
- Are the current processes make your organization to respond appropriately to a breach?
- Do you even know what your aspiring for? What “industry best” looks like? How can you know what you can’t see?
- Do you have enough skilled resources to be as effective as your stakeholders need you to be?
- Have you realistically assessed your security program for People, process, and technology needs?
Information Security Management systems should be reviewed regularly to assess relevance and adequacy. Organizations must focus on forward-looking practices in the following areas of Information Security Management at a minimum.
- Risk management Framework
- Audit functions
- Identity and access management
- Incident/event management
- Procedures for penetration and vulnerability testing/assessment
- Secure procedure for implementing administrative, technical, and physical rule changes
The following are some of the key considerations to cover the growing technology shift and digitization drives.
Define your organizations perimeter
With new boundaries emerging, companies need to assess the extent to which their data is being exposed. The risk management framework should adequately cover the threat vectors and sources to address the ever-changing Information processing ecosystems. Some of the key factors under consideration are;
- Emerging technologies and new business models
- New user experiences and how they are achieved
- Strong practices to address risks in the digitization journey and to integrate security to the fabric of business
- Process to systematically address the risks in changing regulatory landscape across hybrid multi-cloud environment
- Protecting and accessing your data across deconstructed infrastructures
- Ensure security posture in mergers and acquisitions
Identify your upstream and downstream supply chain
Gone are those days where organizations had everything in-house or one strategic outsourcing vendor per service. Today, they deal with multiple vendors with no defined physical boundaries. IBM XForce Research indicates that there will be 990M misconfigured cloud servers that include publicly accessible cloud storage, unsecured cloud databases, and improperly secured rsync backups, or open internet-connected network area storage devices contributed to the exposure of more than 990 million records in 2018.
The complexity is further increased with more devices and IoT devices getting connected to corporate networks. Information security teams need to review the following aspects to re-model their Information security management systems to cater to the expanding boundaries;
- Comprehensive asset management and Configuration Management Database (CMDB) including on-prem, cloud, and other information processing devices
- Contracts with clear segregation duties for the security of the cloud and in the cloud conditions.
- Tightly coupled contracts with IOT device vendors and other service providers covering necessary security controls such as patch management, periodic vulnerably assessments, Penetration testing, and regulatory compliance
- Access management practices to meet the same or higher level of controls as the regular employees
- Security orchestration and correlation platforms encompassing information processing systems together
Make best use of automation and Machine learning platforms
The exponential increase in the ‘things’ to protect need not be directly proportional to the operational costs. This could be increasingly complex and could prevent security teams to work more on reactive mode. Done right, a strong Information Security Management program can provide added business value by reducing IT management costs, enhance employee productivity, and increase compliance efficiency. This is the best time to make the best use of automation, real-time monitoring, encryption, analytics, and compliance to protect the critical assets while keeping the operational cost low.
Tools, techniques, and provisions, that can let organizations leverage automation and analytics should be considered while revamping the Information Security Management programs. There will not be one single tool that can do it for all but could be a carefully designed combination of third party tools, automation initiatives, and market leader insights.
Review skill matrix and team structure
Security organizations within companies are usually smaller ones compared to other technology teams. There are many traditional roles in security such as analysts, auditors, compliance specialists, etc. With new tools, new architectures, and a new set of third-party service providers to interact with, organizations need a completely different set of skills needed for their security function, which they are not prepared with. On the other side, it is unreasonable to expect that there should be a proportionate increase to the team size with new domains getting added under the Information Security Management function. Security in itself is an emerging skill with a huge skill shortage, it is not practical to hire from the market. A well-planned approach to the Information Security Management team composition will help organizations to keep their operational costs to the minimum while keeping a high performing, highly skilled team.
Following are some suggestions;
- Review the current skill matrix and design a talent development plan
- Align budgets for training and certifications
- Not all skills need not be in-house, leverage Security service providers and consultants to augment your teams with skills that are not available in-house
- Continuous review of team skill matrix and upskilling
Summary
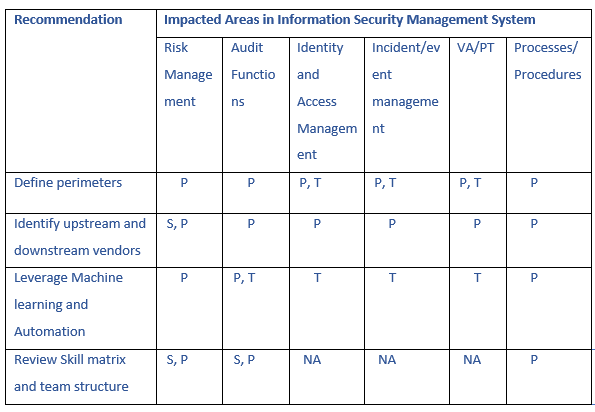
People- S, Process- P, Technology- T
There is no such time to pause and press the reset time for security. There will be a never-ending madness of adding yet another point-product that can’t interact with your existing technologies as promised. It’s time we shift to a more holistic yet simplified and proactive method of driving security as a closely-knit function to support business innovations. This can be executed only through an adaptive, scalable, and resilient Information Security Management function.
By Lekshmi M Nair
Senior Managing Consultant, IBM Security
New Delhi, India

