
Exploiting a Router Are you ready to protect it?

Nowadays, routers are an integral part of today’s home and small office networks. Usually, these kinds of devices are implemented in many places with the default configuration and are, typically, managed by people who do not have any special technical knowledge. Often poorly configured and vulnerable, such devices are an easy target for network-based attacks, allowing cyber-criminals to quickly and easily gain control over a network. I bet you heard the latest news about the “Infected 500,000 Devices That Could Cut Users Off from The Internet”. Over Half a Million Routers infected by Destructive VPNFilter Malware. In this article, we explain how to get admin credentials the in Connect Box DOCSIS 3.0 Voice Gateway router it was possible sniffing the HTTP traffic packets, within the same tested network, and perform some tests it is possible to discover a vulnerability in the authentication process known as Cleartext Transmission of Sensitive Information. This router that has been tested is in Poland by the internet service provider UPC. This company provides services in many EU countries. This flaw is registered in through CVE – CVE-2019-19967 (https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-19967) and according to National Vulnerability Database-NVD this vulnerability has been signed by base score: 7.5 high (https://nvd.nist.gov/vuln/detail/CVE-2019-19967).
1- Connect Box – UPC Router
The Connect Box is the worldwide most compact EuroDOCSIS 3.0 Voice Gateway which provides the ideal all-in-one wired and wireless solution, designed for your home, home office, or small business/enterprise. It can be used in households with one or more computers capable of wireless connectivity for remote access to the wireless gateway.
The purpose of this exploration is to validate the security applied to the standard implementation of the router, as well as to guarantee the application of the main security models, whether in a home user or in a corporate environment.
We performed this proof of concept to get obtain the administrator credentials of the Connect Box DOCSIS 3.0 Voice Gateway router, it was possible to successfully perform, when sniffing the HTTP traffic packets, within the same tested network, when we perform some tests we discover a vulnerability in this router in the Authentication process known as Cleartext Transmission of Sensitive Information.
After discovering this flaw, we communicated the manufacturer about it, which put us in contact with the development team to assist in the improvement process, we also registered this failure through CVE – CVE-2019-19967 (https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-19967)
This router that has been tested is in Poland by the internet service provider UPC. This company provides services in many EU countries.
2- Understanding Authentication Process
The first step in this kind of exploration is to understand how the application handles with the authentication process, as well as, the responses that are “printed” on the authentication page.
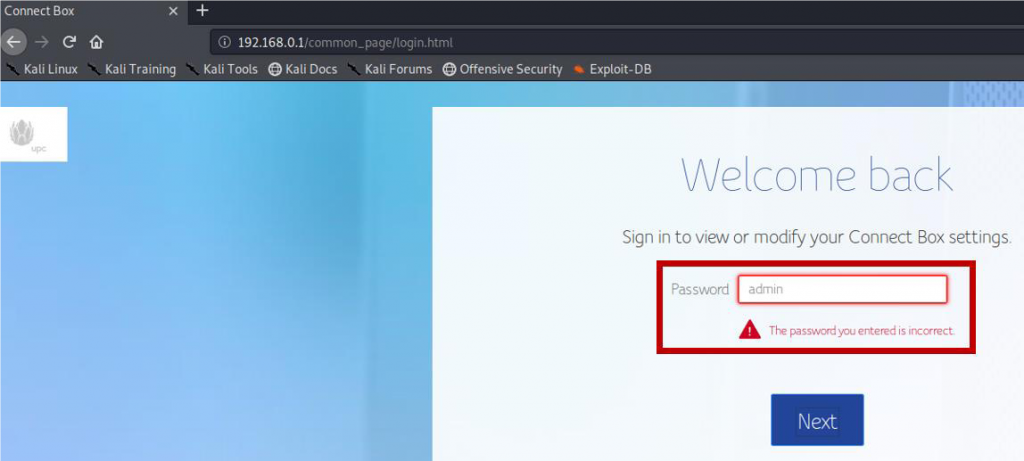
When putting this information in the application (tried “admin” access), we received the error return, as you can see in figure 1, but the text in the box doesn’t in the password for, after that, as you can see in the in figure 2, about the input form it is with type as “text”.
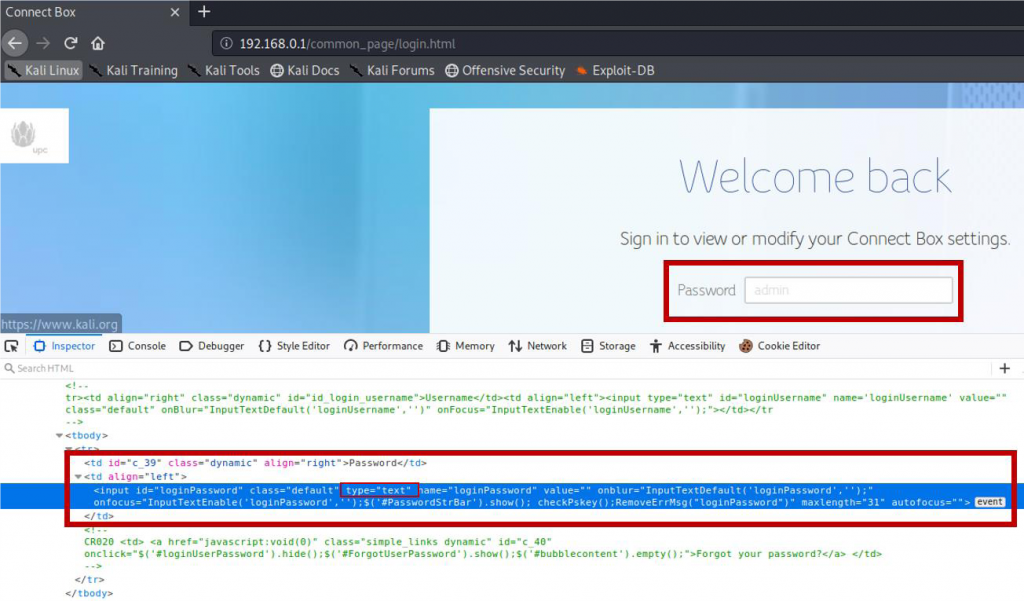
Figure 2: created by owner (2020)
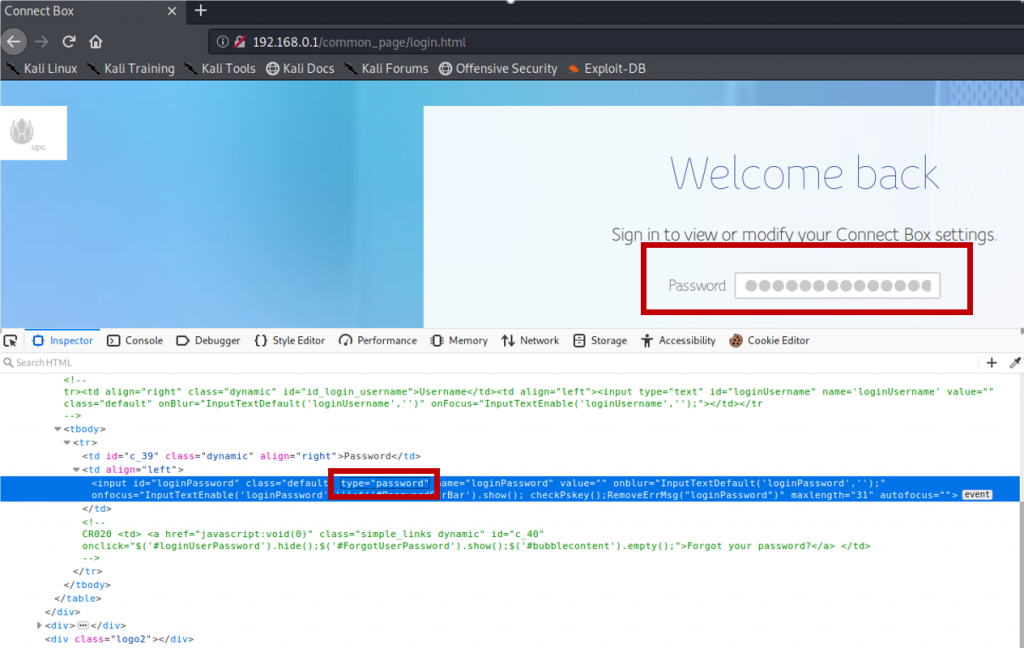
In this case, a recommendation it is used in the input form to this authentication input type=password, as you can see in figure 3. However, this would be just visual protection, we still can’t know how the password treatment is done, when and how authentication is performed, for that we need to use some network sniffer to check how this request and return authentication works in the network communication.
2-Looking Network Communication
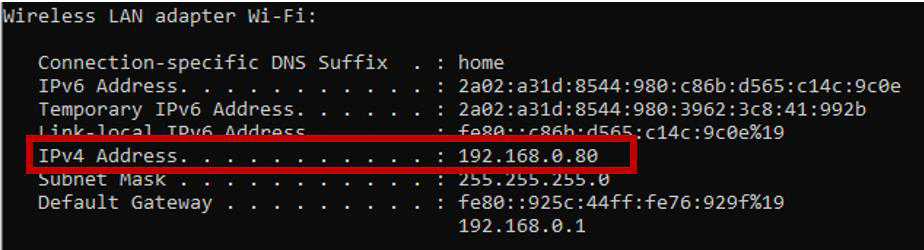
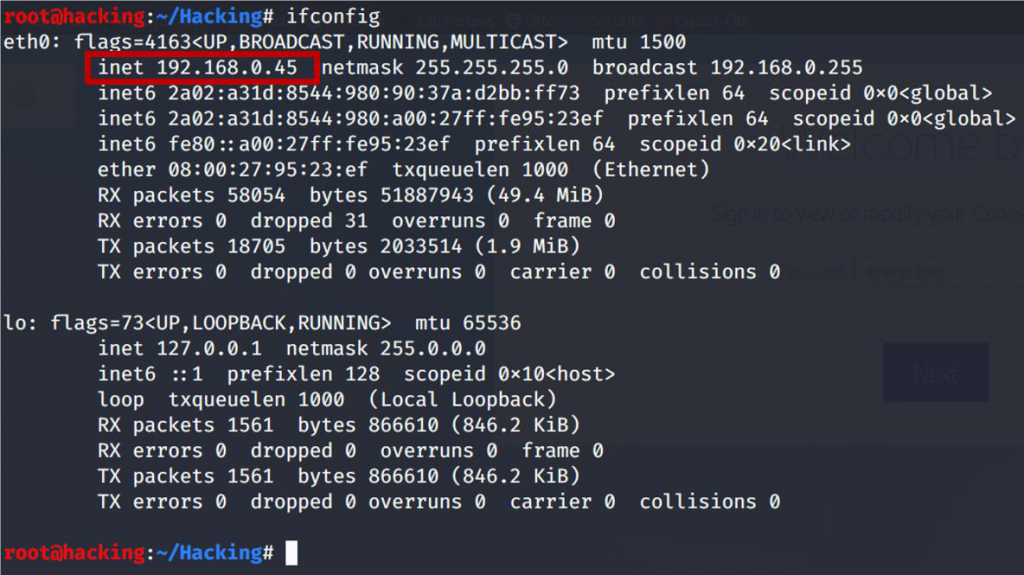
I have been used the attacker machine with the IP Address: 192.168.0.45 to run the Wireshark and received all traffic the network, after that, I’ve used victim machine – Victim 1 – 192.168.0.80.
3-Wireshark Analysis.
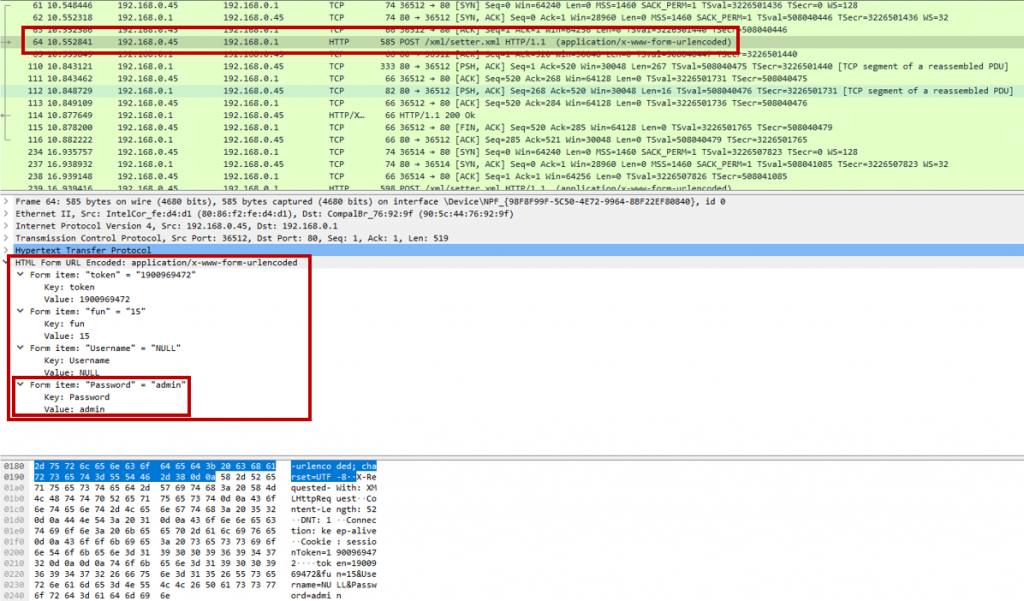
We tried to access with the password “admin”, however, we receive the “login incorrect” information printed in the web page, so we went to see how Wireshark received this Authentication, my intention here, it was to discover, what kind of encryption for authentication the application has used, but for my surprise, as you can see in figure 6, the authentication use none encrypt process the password is a pass in the network in clear text, in this case, we can think about vulnerability known by MITRE as Cleartext Transmission of Sensitive Information ( http://cwe.mitre.org/data/definitions/319.html).
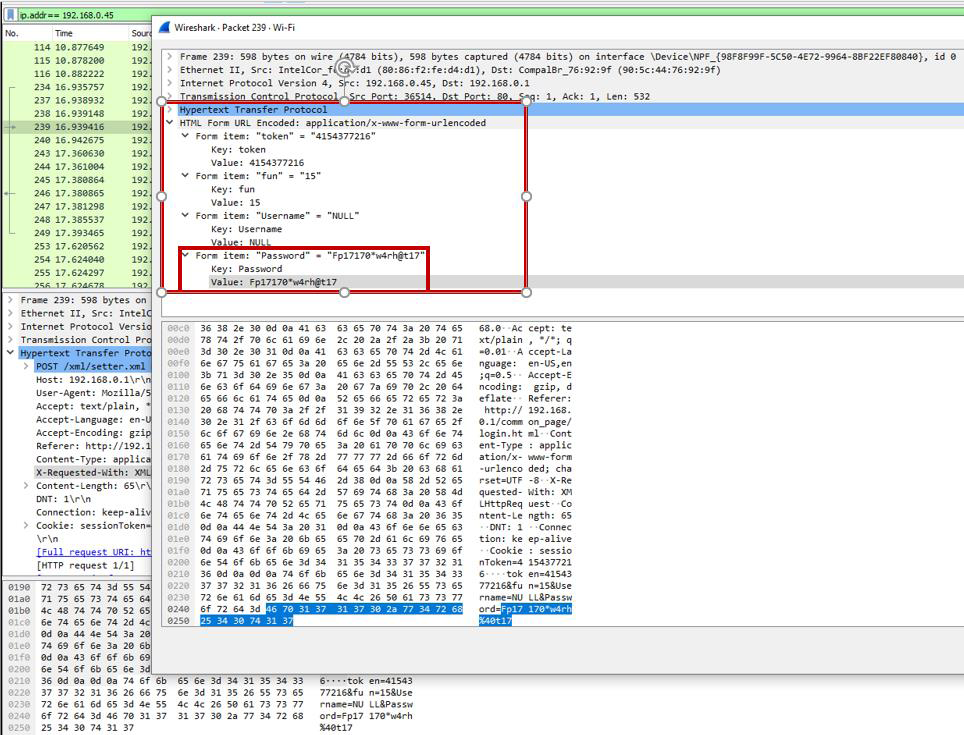
So now, we just need to receive a valid authentication, when you try to connect with your correct password, just be happy, because the Admin Authentication, it will be in Clear Text, for anyone that is receiving network traffic in the same network.
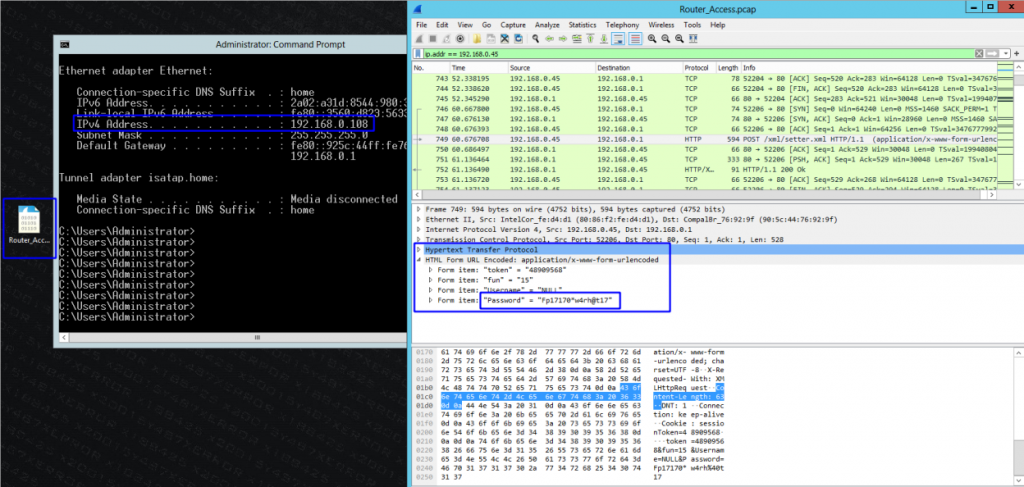
Another important point is, If an attacker has access on this pcap file in another machine, as you can see in windows machine below (figure 8) when this attacker opens in the Wireshark and he starts to analyze this file, we can see the same behavior in authentication process in clear text without simple protection
4-Conclusion
As we can see in this article, a simple cryptographic flaw in the process of web page authentication can greatly compromise the security of a home user when a company that uses this router, this vulnerability it is known as the software transmits sensitive or security-critical data in cleartext in a communication channel that can be sniffed by unauthorized actor and it was signed as CVE-2019-19967 (https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-19967)
You can configure a web application with some type of hidden, encoded, protection, or then some authentication with encryption, or based on some token, so there are many ways to increase the security level of your router.
So, I recommend reading some RFC – HTTP Hypertext Transfer Protocol, to understand the operation, as well as ways of protection.
References
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-19967 – Access at 16/01/2020
https://nvd.nist.gov/vuln/detail/CVE-2019-19967 – Access at 27/08/2020
https://github.com/filipi86/ConnectBoxDOCSIS-3.0 – Access at 16/01/2020
RFC 2660 – https://tools.ietf.org/html/rfc2660 – Access at 16/01/2020
RFC 7231 – https://tools.ietf.org/html/rfc7231 – Access at 16/01/2020
RFC 2818 – https://tools.ietf.org/html/rfc2818 – Access at 16/01/2020
RFC 2612 – https://tools.ietf.org/html/rfc2616 – Access at 16/01/2020
http://cwe.mitre.org/data/definitions/319.html – Access at 27/01/2020 Official Document form UPC – https://www.upc.ch/pdf/support/manuals/en/internet/ConnectBox/connect-box-manual.pdf – Access at 16/01/2020
By Filipi Pires
Research and Cyber Security Manager at Zup Innovation and Global Research Manager at Hacker Security
São Paulo, Brazil

