
Risk surrendering Users in Home!

Nowadays, we have seen a great health struggle against that we know as COVID-19, an invisible pandemic, that we don’t know where it comes from, where it spreads, and/or how it spread so quickly around the world. When we speak of the cyber world, we are often struggling with a similar “type of” enemy. We often don’t know how these malicious artifacts are created, where they come from, what type of vaccine it would be important to have to contain this type of pest, or if already have any vaccine, but this time we go talking about something that is connected by the internet. When we work at a company, usually many corporations offer us a set of platforms to work safely, but when we need to work from home, how do we increase our level of security? How can we be safe at home, without having several security solutions? Throughout this paper, we will be showing some types of attacks and suggesting some actions that do not depend on solutions so that we can increase our level of security in this period of the pandemic.
Introduction
The big volume of information circulating around about the new coronavirus leads to the existence of new dangers such as the massive spread of phishing attacks, this kind of attack seeks to exploit the social fear installed over the sometimes-deadly virus.
COVID-19 is being used in a variety of malicious campaigns including email spam, phishing, ransomware, different kind of malware, websites malicious, and malicious domains. As the number of those afflicted continue to surge by thousands, campaigns that use the pandemic as a bait increase as well.
So, in this case, how it works?
Cybercriminals send emails claiming to be from legitimate organizations with information about the new coronavirus.
Email messages may ask you to open an attachment to view the latest outbreak statistics. By clicking on the attachment or the embedded link, you will probably be downloading (often without your knowledge) downloading malicious software on your device.
Malicious software – Malware – can allow cybercriminals to take control of your computer, accessing your personal information, recording all the information you type using your keyboard, and financial data, which lead to situations of identity theft.
Researchers from cybersecurity companies like Trend Micro, Trustwave Holdings, and Sophos warn of types of strategies used in email phishing that take advantage of some users’ panic over the Coronavirus outbreak (COVID-19). Cybercriminals impersonate entities such as the World Health Organization (WHO) or the North American Disease Control and Prevention Center (CDC), disseminating false information and leading victims to compromise the security of their personal data and devices.
Types of Threats using COVID-19
When we talk about working from home, we know that users who are often connected with their personal laptop, end up lowering their attention on Cybersecurity, making them easy prey for attackers.
During this paper, we will talk about some forms of attack used by the attacker aiming at working from home and we will bring some tips to avoid being attacked and having our data leaked.
Let’s go the most common attacks.
PHISING MALICIOUS LINK
When it comes to cyber-attacks, all research by security company’s points to the main vector of entry for companies and home users, which are attacks known as Phishing, this attack is the fraudulent attempt to obtain confidential information, such as user, passwords and credit card details, disguising themselves as an email or trusted person in electronic communication. Usually performed by spoofing email or instant messaging, it often directs users to enter personal information on a fake website, which matches the look of the legitimate website.
Quick Tip
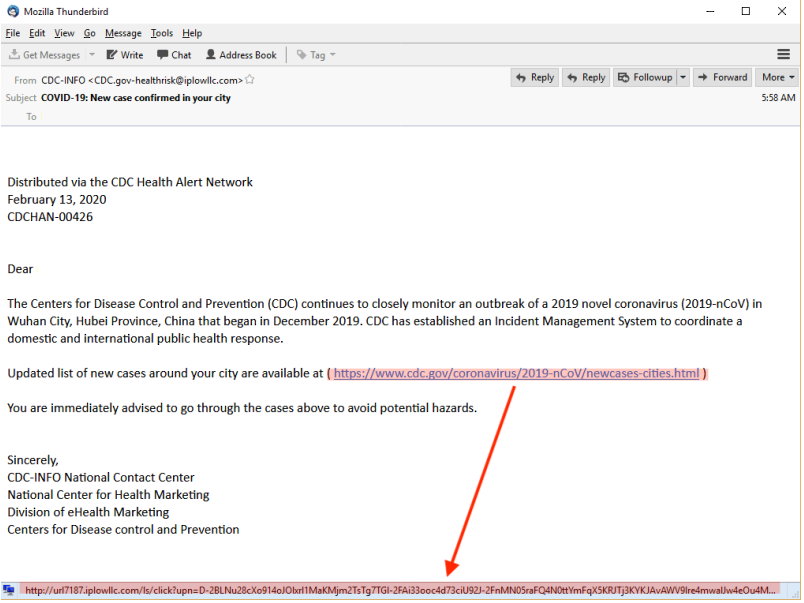
The first recommendation for a user who receives an email is always to look at who the sender of that message is, locate the email of the person who sent it to you, this information is located after the “@”, looking at the domain of the “person” who sent this email to you, now you can check if it’s potentially malicious email.
A second recommendation is to look if there is any URL in the body of the email, and as we can see, by placing the mouse over the “URL” we can see at the bottom that it shows the actual website that will be connected, and noting that they are different we can learn that he will be redirected to another website, not the true website, that is, another sign that he is potentially malicious.
SPAM MALICIOUS EXTENSION
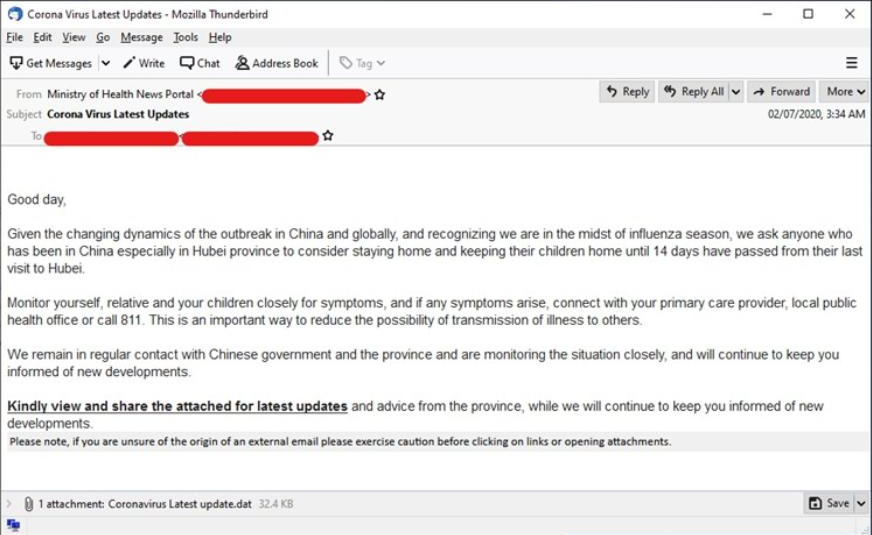
When do we look at the example bellow, who is in the Security area already noticed that the attached file is a file with a .dat extension, but what is exactly a DAT?
ADAT file is a generic data file created by a specific application. It may contain data in binary or text format (text-based DAT files can be viewed in a text editor). DAT files are typically accessed only by the application that created them, that is, this DAT was made to run some application on your machine, that is, almost 100% of which we will have a malicious file being installed on our equipment.
Quick Tip
When we receive an email, we need to look at what is the extension of the file that is attached, we must be careful with type extension: exe, bin, day, CPL, etc.
SPAM DOC EXTENSION
Seeing that people have learned more about Cybersecurity, the attackers returned to bring the attacks related to Maldoc (Document Malicious), that is, Word, Excel, and PDF files, with malicious embedded scripts, sometimes depending on a macro activation, or an action to open a particular PDF.
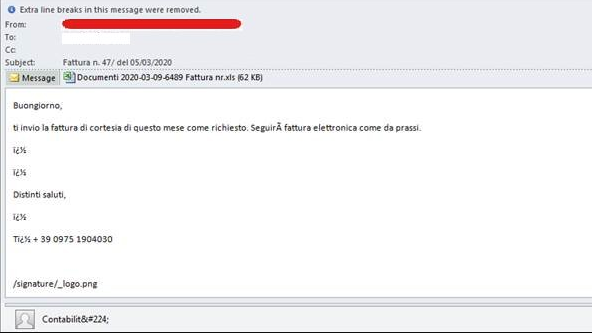
Other samples of email spam targeting Italy were also detected by Trend Micro researchers¹. This time, mentions of the disease were not found in the email subjects, but in the URL. The subject instead contained the word “Fattura” (Italian for “invoice”) and the body as well, the invoice number, and its supposed date.
The emails had attachments that contained malware, which executes a PowerShell command that will download a file from a URL related to COVID-19. The URL is https://recoverrryasitalycovid-19.xyz/over.
Quick Tip
When you receive an email with one with an attached doc, such as .doc, .xls, PDF among others, locate the email sender, and validate whether that email makes sense to be sent to you.
Another recommendation is if a Word Doc, Excel Doc, PDF, among others redirects you to a website, it is certainly suspicious and should not be clicked, and you should never enter your personal data on any of these malicious sites.
SMS MOBILE ATTACK
Other examples we see are linked to SMS with a focus on Information theft, where the user accesses many pieces of information by mobile.
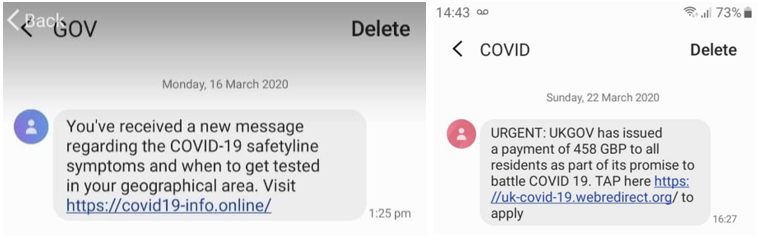
Many users have received SMS on their cell phone, with information related to COVID-19 as we can see, with a link that would “give” access to symptoms and others information, and in another example we see the attacks taking advantage of the financial that many countries have provided in this period of crisis, requesting access to a website with “fake” where the attacker collects all the user’s private information.
Quick Tip
Always be careful with any SMS received by an unknown number, always validate who the sender of that message is, in addition, WHO has already issued a statement that alerts the population to the use of their name and image in fraudulent schemes, whether by email, by SMS or even by phone calls. The organization clarifies on its website that it never asks the public to enter access credentials to be able to access information or to visit an address outside its network of pages.
Conclusion
In this article, we saw how challenging it is to work in a different environment than we are used to.
Working from home has its advantages, but when we talk about the cybercrime scenario, it becomes a little more complex, especially for those who do not work with cybersecurity.
Our enemy is totally invisible; we fight against a kind of attacker that usually it is a step ahead.
We often do not know how these malicious artifacts are created, where they come from, what kind of vaccine would be important to contain this type of pest.
Throughout this article, we saw that when we received an email, we should to look for who is the sender of that message is, when we looking at the domain of the “person” who sent this email to us, now we can check if it’s potentially malicious email.
We should look at the type of extension that is attached to the email, if it is an executable, binary, Word Doc, PDF, among others, we need to be very careful when opening all types of files.
We have come to see that attackers have used many messages by SMS to also collect information from their victims.
As a result, we hope that you can increase your security level a bit in this pandemic period.
References
https://apav.pt/apav_v3/index.php/pt/2278-covid-19-como-se-proteger-das-burlas-e-mails-de-phishing
By Filipi Pires, Senior Security Systems Engineer
Cracow, Lesser Poland District, Poland

