
Zero Trust in an Age of Coronavirus (COVID-19)

The sudden shift to remote working for some organizations and the acceleration of a work-from-home culture introduces new risks.
Today, being hit with a data breach is almost inevitable. No organization is immune and even government agencies have been victimized. Now, experts are predicting more serious repercussions than data theft including data and system manipulation, and full exposure of company secrets and intellectual property. At the same time difficulties in enforcing data protection have never been more challenging—and more urgent.
• Trust is no longer determined by location or IP address.
• There isn’t a distinction between “inside” the network or “outside” the corporate network any more.
Most attacks result from compromised credentials, vulnerable endpoints, unmanaged IoT devices, or unprotected access to applications and resources. Attackers gain an entry point to a network and begin to discover resources and expand control. But organizations are also vulnerable to unintentional mistakes: in a recent study, human errors were the second largest cause of data breaches.
And while each organization needs to take their own unique circumstances into account, organizations need to focus on protecting identities and applications regardless of whether they are in the corporate network or the cloud. The Solution is to implement Zero Trust
Zero Trust is a network security model that trusts no one, regardless of their location. Increasingly, trust can no longer be established based on whether a user is “inside” or “outside” the network. Every user is vetted before – and during – a connection, and every connection is governed by a policy that controls what resources can be accessed.
Leveraging Zero Trust means that enterprises enhance their security posture by:
- Validating users, and their devices’ security posture.
- Controlling access through granular policy enforcement.
- Protecting and encrypting data transactions.
By implementing the following recommendations (see mind map), organizations can reduce the ability of unauthorized access in remote access solutions.
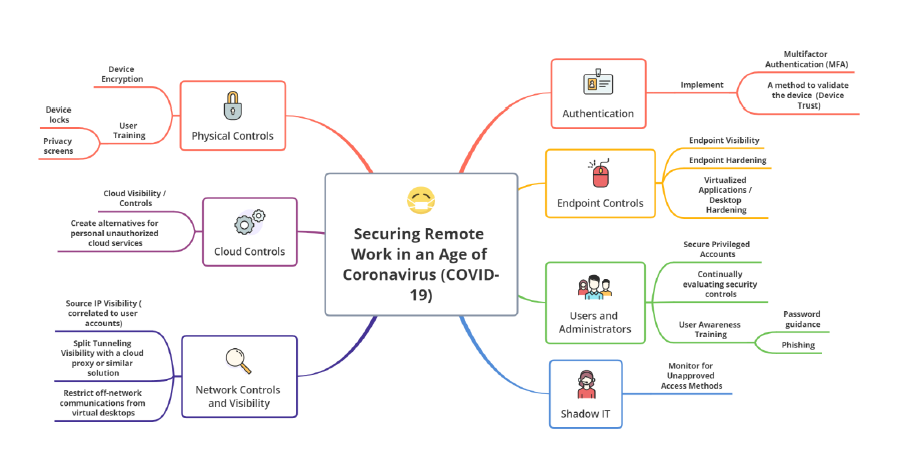
Authentication
• Multifactor Authentication: Organizations must implement MFA on all external corporate resources to reduce the ability of network and application access through credential spraying, password stuffing and phishing attacks. Review all external corporate resources, including cloud services and their configurations. Disaster Recovery (DR) and legacy VPNs must be considered in-scope when reviewing all network connectivity authentication, as these may maintain single-factor authentication settings.
• Device Trust: Organizations should not stop at MFA. Implement a method to validate the device establishing connectivity is a known device managed by the employee. This can be accomplished by utilizing a system management platform that places identity certificates in the device’s Trusted Platform Module (TPM).
Endpoint Controls
• Endpoint Visibility: Many organizations lose visibility into malicious activity targeting remote workers. Organizations should deploy a multi-layer endpoint agent on all employee endpoints. The endpoint agent should be able to detect, protect and respond to malicious activity.
• Endpoint Hardening: Harden devices to reduce the ability for an attacker to gain access to systems and escalate privileges. Local administrator rights should be limited, and systems should be hardened to a common baseline standard such as CIS benchmarks (https://www.cisecurity.org/cis-benchmarks/).
• Virtualized Applications / Desktop Hardening: Default configurations of virtualized interfaces may allow the ability to ‘break out’ of virtual sessions, allowing access to the underlying operating system.
Users and Administrators
• Secure Privileged Accounts: Privileged users, such as domain administrators, should maintain separate accounts and be prohibited from remote access using their privileged credentials. These privileged users should escalate access when necessary on a dedicated Privileged Access Workstation (PAWs) dedicated to these accounts.
• Continually Evaluating Security Controls: As networks grow and change, security controls may weaken over time and legacy systems may be unmanaged. Avoid environmental drift by continually evaluating security controls through red and purple team exercises.
• User Awareness Training: Provide security awareness training for remote workers. In addition to computing hygiene topics such as phishing and password guidance, train employees on physical security topics such using a privacy screen, limiting work on confidential material in public spaces and securing physical computing assets.
Shadow IT
Monitor for Unapproved Access Methods: As remote access needs dramatically change; organizations will likely be faced with employees and third parties attempting to stand up services in an unapproved manner. Security teams should continue to monitor for unauthorized remote access methods through regular vulnerability scanning, proactively engaging business units and penetration testing.
Network Controls and Visibility
• Restrict Off-network Communications from Virtual Desktops: If some external network access is required, maintain a whitelist inclusive of only necessary, approved resources to limit exposure.
• Split Tunneling Visibility with a Cloud Proxy or Similar Solution: Though shifting from full-tunnel to split-tunnel VPN may be necessary; it may restrict outbound endpoint visibility. Consider augmenting network visibility with a cloud proxy or similar solution. While that will not cover all the communication methods, it does cover popular ones. Be sure to review DNS logs for remote endpoints.
• Source IP Visibility (Correlated to User Accounts): Depending on the network topology, identifying the origination IP address for traffic may be hindered by load balancers, proxies, DNS configurations and DHCP pools. Ensure that any traffic originating from the VPN can be appropriately tied to source IP address, and assignment of IP addresses can be determined and appropriately correlated to user accounts.
Cloud Controls
• Create Alternatives for Personal Unauthorized Cloud Services: Employees may start using third-party solutions for note taking, file storage and document management. By implementing corporate alternatives, organizations can ensure that corporate data is protected and monitored by corporate security controls.
• Cloud Visibility / Controls: Cloud services are an important resource for remote workers and can contain sensitive corporate data. Ensure that teams are receiving logs from cloud providers and regularly reviewing them for unauthorized access and data
exfiltration. To limit unauthorized access, configurations should be assessed and controls reviewed on a regular basis.
Physical Controls
• Device Encryption: Organizations should consider the potential for laptops to be lost or stolen. Ensuring that all employee computing resources have full disk encryption enabled will help protect corporate data in the event the resource goes missing. Be sure that full disk encryption controls have a solid strategy around key and password management.
Resources
https://pulsesecure.allbound.com/engage/demystifying-zero-trust-network-access-ztna-ebook/
https://www.fireeye.com/blog/executive-perspective/2020/03/remote-work-in-an-age-of-covid-19-threat-modeling-the-risks.html
By Ahmed Allam
Presales Manager|Cyber Security Solutions Architect

