SCADA Penetration Testing

Supervisory Control and Data Acquisition systems simply are known as SCADA defines Industrial Control Systems (ICS) that are used for controlling and monitoring the Infrastructure of industries. SCADA systems are used by organizations to automate the complex industrial process. Just like the normal networks have protocols these systems have their own protocol such as DNP3, Modbus, IEC 60870, BACnet, Lon Works, and EPIC. SCADA data are encoded into protocol format. Older SCADA systems depended on closed proprietary protocols, but today the trend is towards open, standard protocols and protocol mediation. The remote telemetry (or terminal) unit (RTU) or the programmable logic controller (PLC) is needed to provide an interface between the field instrumentation and the SCADA network.
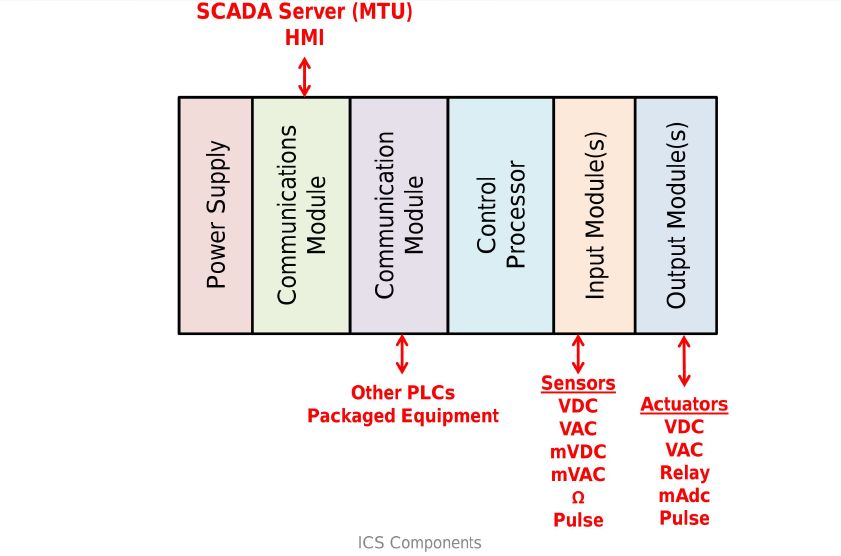
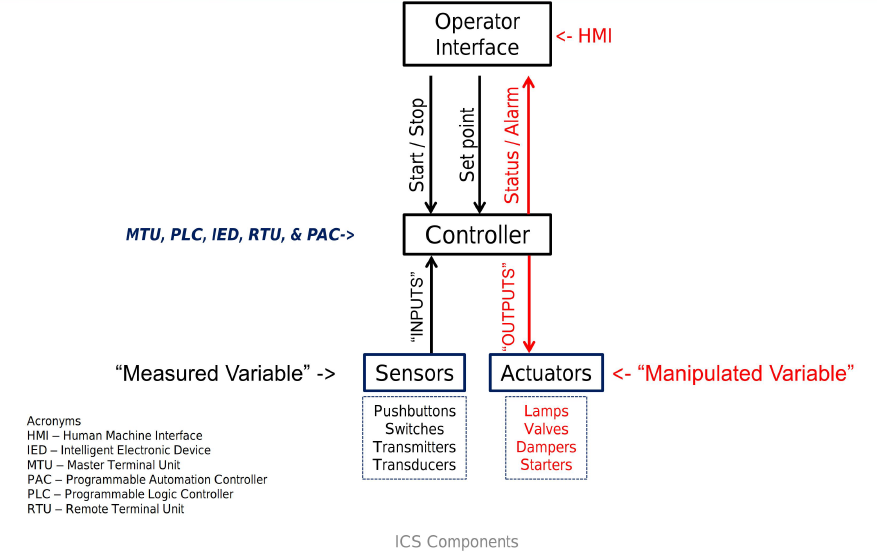
The systems to be monitored by SCADA has hundreds of devices such as sensors, actuators, switches, valves, transmitters, meters, and drivers. They can track fluid levels in tanks, voltage levels in batteries, temperature, and any other factor that can be measured in a continuous range of input. The emergence of the PLC led to a host of logic-based digital systems, such as Supervisory Control and Data Acquisition (SCADA), Distributed Control Systems (DCS), and others. Heating, Ventilation, Air Conditioning (HVAC); building elevators; smart meters on the sides of our homes; SCADA systems and sensor networks in substation automation and power grid transmission distribution; robotic control in auto manufacturing; and food and beverage packers are few examples of how Control System is used in our daily lives. The below diagram shows the basic Control System Components.
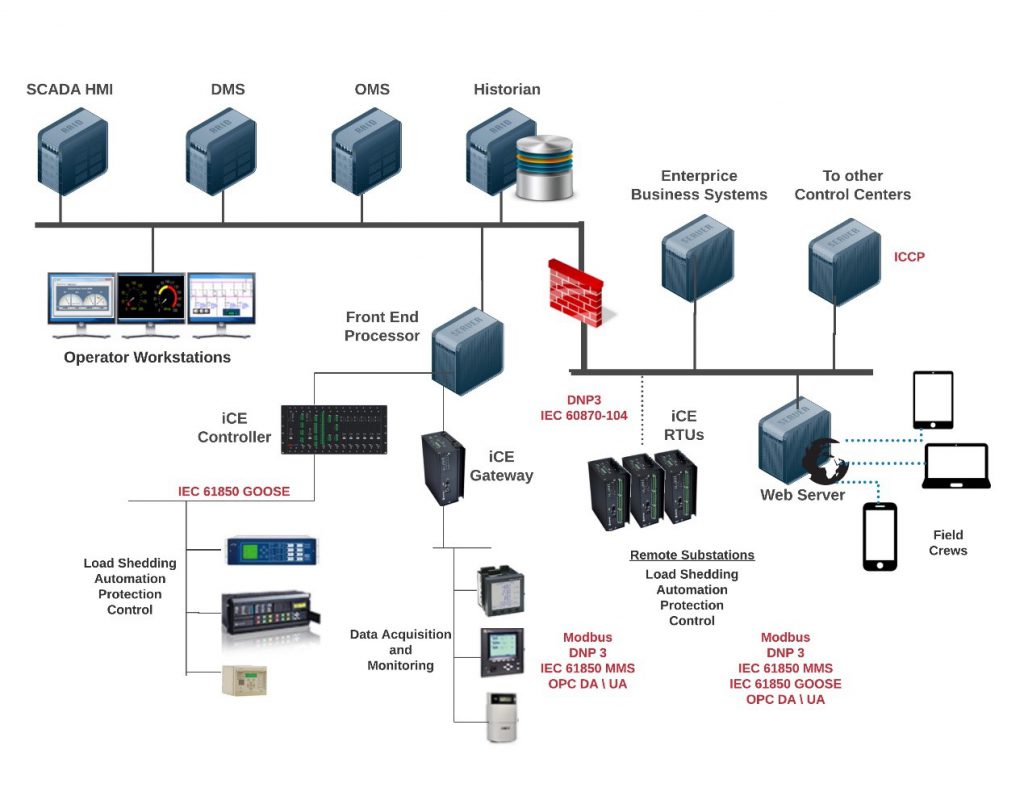
Computer software used within the system is an important component of a SCADA System. A successful SCADA system is likely to result when the software is well-defined, designed, written, checked, tested, and deployed. Depending on the size and nature of the application, SCADA software can be a significant cost item. When software is well-defined, designed, written, checked, and tested, a successful SCADA system is likely to result. Usually, SCADA software is configured for a specific hardware platform. Due to the growth in SCADA systems, there is a wide range of general SCADA software products available which is more flexible and compatible with different types of hardware and software. SCADA software products provide the building blocks for the application-specific software
SCADA System Architecture Key Features
- Seamless integration
- Robust client/server architecture
- Multi-redundant system
- Scalable modular design
- ODBC / SQL compliant database
- Enterprise-wide access
- Multi-tiered user access management
- ISO 9001 A3147 certified
- Hardware independent
Most of the SCADA systems are outdated legacy systems. Patches or updates are not implemented the same as how it is done in IT Infrastructure as industries don’t want to risk their production line malfunctioning due to untested patches. In terms of security, patches and updates are too infrequently incorporated into the product lifecycle. In addition, when a vulnerability is unveiled on one of the components, it is difficult to interrupt the production chain until the patches are applied. There is a tendency not to patch SCADA systems for fear of breaking something. This can leave gaps in your digital defense which attackers can easily exploit. Due to this reason, it is very much important to conduct Penetration Testing to ensure that proper security mechanisms are in place.
There are two important issues, namely communication security and system reliability that significantly impact the application of SCADA networks. The concern about communication security arises due to the fact that nowadays most of the SCADA networks are not isolated or independent networks. Most of them are linked or merged with other industrial control systems or computers. The interconnection between SCADA and other networks requires compatibility with different communication standards to move data from one unique system to the other. Due to the complexity of addressing different protocol standards, network administrators often fail to secure them due to the burden of associated security risks and so access control is minimal. Another problem is that while designing SCADA networks the architect will forget about the security strategies like segregating the SCADA network from other networks and or placing a firewall in between these networks.
Long term successful operation is dependent upon the SCADA system’s reliability, that is, the quality and performance of the equipment. A Telemetry system is a complex engineered system that has many possibilities of failure. This includes failure due to human error or operating documents, to design flaws, from software applications to implementation, to environmental conditions, or due to redundant equipment failures, etc. This range of difficulties makes it difficult to completely analyze the reliability of SCADA systems encompassing all these factors. So we can say that reliability analysis is just an approximation of the worst factors. But now methodologies are evolving to include human error factors, redundancy equipment failures, software failures, etc.
The resulting impact that can occur when ICSs fail to perform (or are made to not perform) their intended functions include the following:
| • Catastrophic safety failures • Environmental release of hazardous materials • Loss of production • Product recall • Regulatory fines • Sustained production inefficiency • Loss of public confidence |
Due to the above issues, the Penetration Testing exercise should be carried out carefully on production networks. Organizations conducting Penetration Testing Exercises on their SCADA Network/Systems are rare. If testing is to be started then we separate the testing into six phases (shown in the diagram) and communicate with the responsible person during each phase of the testing.
•Scoping
•Reconnaissance
•Mapping and Service Identification
•Vulnerability Analysis
•Exploitation
•Reporting
Cyber Security Professionals often identify three modes of failure:
- Breach of confidentiality, which is a failure to protect sensitive system information from unauthorized disclosure,
- Loss of availability, which is a failure to provide reliable access to system data for those users or machines that legitimately require it, and
- Violation of integrity, which is a failure to protect system data from unauthorized manipulation.
The cyber risk assessment problem is to determine the degree to which a specified
A Network-dependent system is at risk due to the potential for computer network attack, where risk is due to the potential for detrimental outcomes and their associated consequences. The cyber risk management problem is to determine the relative costs and benefits of implementing candidate risk mitigation policies in terms of resources expended and operational consequences avoided, respectively.
There are many attack vectors available for SCADA systems/networks such as:
- Denial of Service Attack
- Plant trojan and take over the system completely
- Database Attacks
- Common protocol attack
- Man in the Middle attack
- Communications hijacking attack
- Attacks on field device/equipment
Traditional security testing targets corporate networks, systems, and software that reside to provide services to corporate networks and users. SCADA systems have been relatively excluded from security testing.
SCADA systems are increasingly becoming a target for focused attackers – with some highly publicized successful intrusions resulting in malicious attackers obtaining administrative access to core systems.
To ensure your SCADA based systems are secured from external threats, self-assessment and external independent testing should be performed bi-annually.
Pure Security has performed many assessments on SCADA networks and has in-depth experience in assisting clients in integrating security controls into their SCADA environment. Client references are available upon request.
Device/equipment _Why perform SCADA testing?
- SCADA systems are often outdated legacy systems and full of holes.
- Companies today are connecting SCADA network segments to the Internet.
- There is a tendency not to patch SCADA systems for fear of breaking something. This can leave gaps in your digital defense which attackers can easily exploit.
- What you gain from this testing
- A comprehensive understanding of the risks of your SCADA systems.
- Assurance that your SCADA systems can hold up against a motivated attacker.
- A comprehensive report outlining the security issues of your SCADA systems, including high impact recommendations and root causes.
- Peace of mind that the SCADA systems are secure.
How we Penetrate the SCADA?
We customize its testing to your environment and requirements. We have developed a proven methodology to test SCADA systems which can include:
Reconnaissance systems and enumerating SCADA software in use.
• Port Scanning
• Identifying weak access controls.
• Network Equipment Security Controls Testing
• Administrator Privileges Escalation Testing
• Password Strength Testing
• Network segregation.
• Exploitation research.
• Brute Force attacks.
• Denial of service checks.
• Misconfiguration attacks.
• Manual Vulnerability Testing and Verification
• Manual Configuration Weakness Testing and Verification
Rajivarnan R
CEO & Security researcher at Cyberarch Consulting oü
Estonia

